Just how to Pick the Best Cyber Security Services in Dubai for Your Organization Needs
Just how to Pick the Best Cyber Security Services in Dubai for Your Organization Needs
Blog Article
The Value of Cyber Security in Protecting Your Digital Possessions
In today's digital period, the value of cyber security in guarding your digital possessions can not be overemphasized. As technology advancements, so do the techniques of cybercriminals, making robust cyber defenses necessary for organizations and individuals alike. From personal information to essential company details, the danger landscape is ever-changing and vast. Carrying out effective cyber safety practices is not just a necessity yet a suggestion to make certain and mitigate dangers connection. What methods can you take on to remain one step ahead and fortify your digital existence versus these persistent threats? The responses may amaze you.
Comprehending Cyber Risks
In the quickly progressing landscape of electronic technology, understanding cyber dangers is vital for guarding electronic possessions. The term "cyber threats" encompasses a wide range of harmful activities intended at jeopardizing the integrity, privacy, and schedule of information systems.
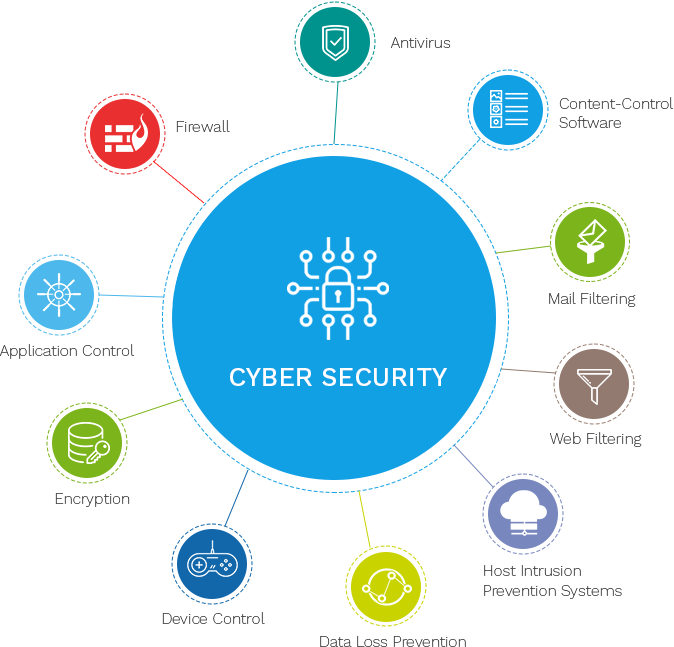
Comprehending the motivations behind these threats-- be it financial gain, espionage, or hacktivism-- is crucial for developing effective countermeasures. This knowledge equips companies to anticipate prospective hazards, customize their defenses, and ultimately shield their useful digital assets from cyber opponents.
Secret Cyber Protection Practices

Network protection is one more vital element - Best Cyber Security Services in Dubai. This includes making use of firewalls and intrusion discovery systems to monitor and manage inbound and outbound network traffic, properly blocking questionable activities. Routinely upgrading software and systems is equally crucial, as it covers known susceptabilities that cybercriminals can make use of
Information file encryption is an important practice that makes certain sensitive information is only available to accredited individuals. By transforming information into a code, it ends up being unreadable without the decryption trick, hence protecting it from unapproved gain access to throughout transmission or storage space.
Enlightening employees and users regarding cyber safety finest techniques is likewise important - Best Cyber Security Services in Dubai. Normal training sessions can raise awareness concerning usual risks like phishing and social engineering, encouraging individuals to acknowledge and prevent potential dangers. By integrating these essential practices, companies can build a resilient defense versus the ever-changing landscape of cyber dangers
Protecting Personal Data
Guarding personal information has actually ended up being a crucial in today's electronic age, where the quantity of info exchanged online is staggering. This information incorporates everything from social protection numbers to personal health and wellness documents, and its defense is crucial for preserving personal privacy and safety and security. People must be attentive in guaranteeing that their individual info is not compromised, as violations can lead to identity theft, financial loss, and reputational damages.

Understanding of phishing efforts is important, as cybercriminals regularly use misleading emails and web sites to take individual info. Individuals need to validate the source of unwanted interactions and prevent clicking on dubious web links. Safeguarding individual tools with anti-virus software program and firewall softwares can additionally strengthen defenses against unapproved gain access to and prospective hazards.
Shielding Company Information
While securing personal data remains a top priority for people, organizations face the wider obstacle of safeguarding large amounts of sensitive details that drive their operations. Executing durable cyber protection measures is not just an alternative however a critical need for organizations of all sizes.
To efficiently safeguard business information, a multi-layered safety and security strategy is vital. This must encompass firewall softwares, file encryption, breach discovery systems, and routine security audits. Furthermore, worker training plays a substantial function in lessening human errors, which are commonly made use of in cyber-attacks. Firms must cultivate a security-conscious culture where staff members understand the value of data defense and are outfitted to acknowledge phishing efforts and other dangers.
In addition, companies need to develop and consistently update occurrence feedback plans. Being gotten ready for possible breaches guarantees quick activity to mitigate damage. By buying thorough cyber safety and security methods, organizations not only safeguard their possessions yet additionally reinforce count on with their companions and consumers, ultimately securing their market setting and future growth.
Future Fads in Cyber Protection
As the electronic landscape rapidly evolves, future fads in cyber safety are poised to redefine how businesses shield their digital assets. These modern technologies make it possible for quicker identification of abnormalities and prospective risks, allowing for extra efficient and automated reactions to cyber incidents.
As remote job becomes a lot more prevalent, standard perimeter-based security designs are confirming inadequate. The zero-trust technique calls for continuous verification of customers and devices, even within the network, thus decreasing potential assault vectors.
In addition, quantum computing is these details arising as both a threat and an opportunity. While it promises unmatched processing power, it positions dangers to existing encryption methods. Organizations needs to plan for post-quantum cryptography to safeguard their data.
Lastly, privacy-enhancing innovations are getting energy. With increasing regulatory focus on data security, services are buying tools that guarantee compliance while preserving operational performance. These future patterns underscore the ever-evolving and dynamic nature of cyber safety and security.
Conclusion
In an increasingly interconnected digital landscape, the execution of durable click resources cyber protection steps is vital to secure digital assets from developing threats such as malware, phishing, and ransomware. Using techniques like solid passwords, multi-factor authentication, and normal software program updates improves the protection of sensitive details, mitigating dangers of identity burglary and monetary loss. Building awareness and taking on sophisticated safety and security approaches foster durability and count on, ensuring the honesty and continuity of both individual and service digital procedures when faced with future cyber challenges.
In today's electronic era, the relevance of cyber safety in protecting your electronic assets can not be overemphasized.Executing effective cyber safety practices is critical in protecting electronic possessions versus developing hazards.As the digital landscape swiftly develops, future fads in cyber safety and security are positioned to redefine how organizations safeguard their electronic assets.In a progressively interconnected electronic landscape, the implementation of durable cyber security steps is crucial to protect electronic assets from developing hazards weblink such as ransomware, malware, and phishing. Structure awareness and embracing innovative security techniques foster durability and trust fund, ensuring the stability and connection of both individual and organization digital operations in the face of future cyber difficulties.
Report this page